
Secure Microstructure Fingerprinting
Every object has its own unique fingerprint that represents its microstructure. Our Vision AI protocol captures these fingerprints using a smartphone or any camera. It functions like a human fingerprint, leveraging physics, computer vision, machine learning, and neural networks. It’s impossible to breach or bypass.
Create your first fingerprint to make your products more secure and intelligent
The entire process is managed automatically using our Vision AI protocols as follows:
-

Step 1
Choose the right fingerprint to meet your business needs.
+ Select -
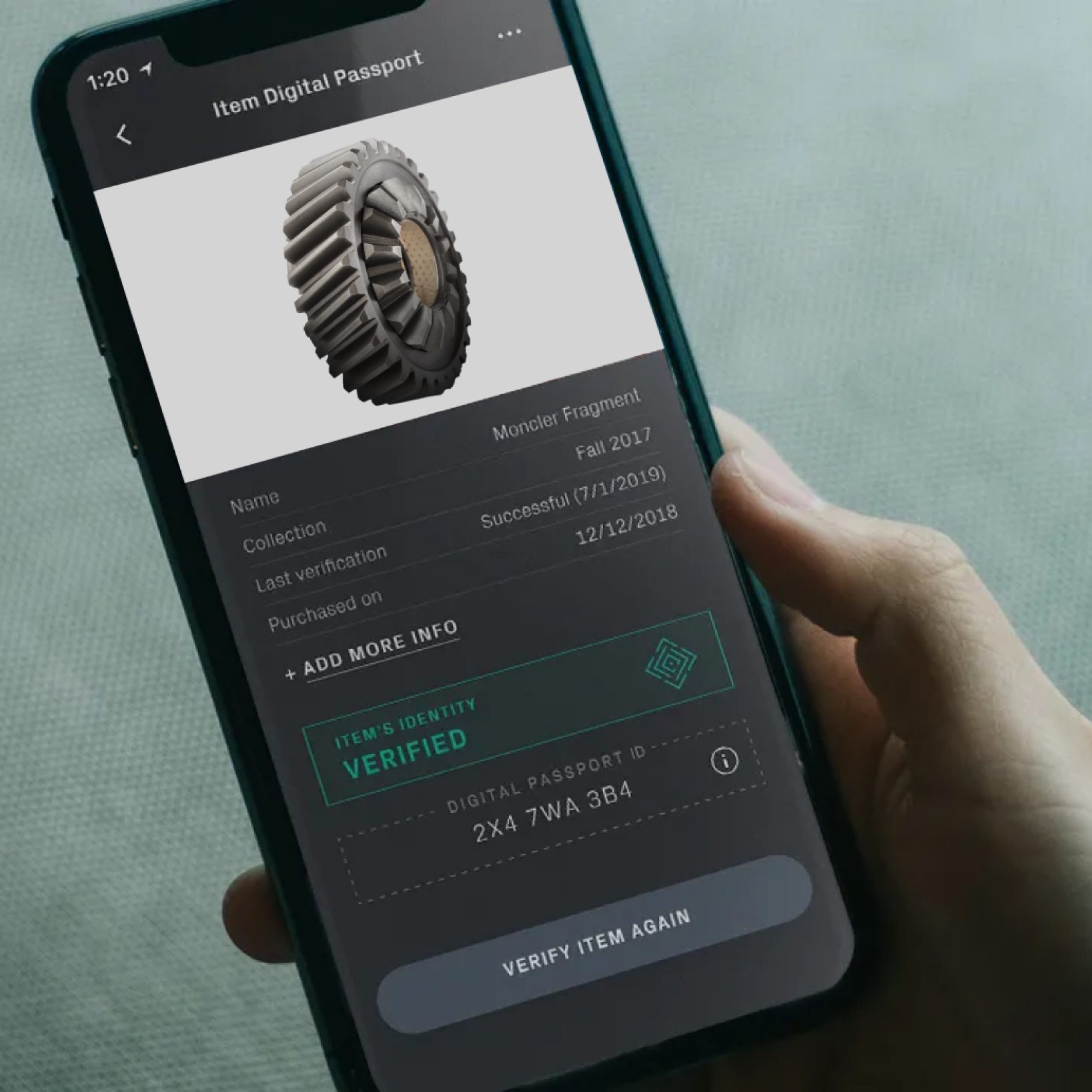
Step 2
Take an image of your product or collect SKU samples using any smartphone or camera. -

Step 3
Analyze the product's microstructure and extract its unique randomness. -
Step 4
Capture a fingerprint as a tamper-proof unique identifier. -
Step 5
Store all data in your library for further monetization and management.
Leverage the scalability across all materials and industries
Our protocols are the backbone of your solution, delivering seamless functionality across any infrastructure, hardware, or software environment.

Secure Non-invasive Serialization
links a unique, non-invasive microstructure number (NMN) to your products, ensuring they can be securely serialized and individually identified.

Secure Microstructure Authentication
verifies the genuineness of your products with the highest level of accuracy, ensuring they are not fraudulent or counterfeit.

Image-based Product Classification
categorizes your products into predefined classes and provides accurate identification by analyzing digital images with top precision.

Secure Digital Product Passport
represents the product itself through its microstructure, eliminating the risk that identifiers or data carriers could be compromised or forged.

Secure Product Traceability
tracks untraceable products without tags, chips, codes, or printing elements with the highest security and ESG status across the supply chain.

Secure Product Integrity Detection
monitors unauthorized modifications and detects any anomalies in your products, ensuring they meet original specifications.
Maximize security and data management
Our Vision AI protocols handle data formatting, camera operations, material analysis, dataset creation, model selection, alignment, GPU and API management, and cross-platform security.
Monetize your fingerprints with every use
Our protocols automatically manage the entire process with the highest level of security as follows:
-

Step 1
Store your fingerprints for future use and transparency. -
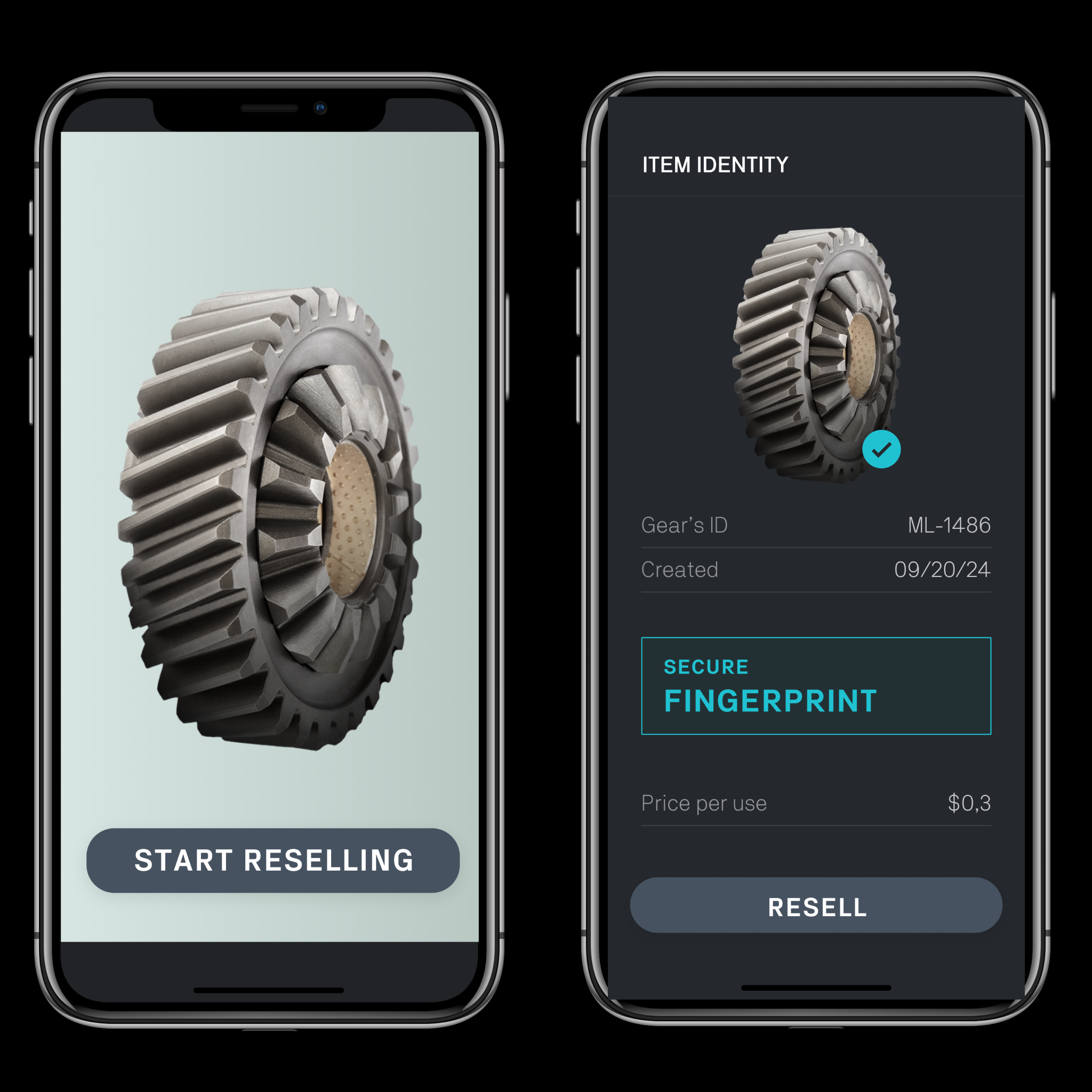
Step 2
Set rights and pricing for reusing your fingerprints. -
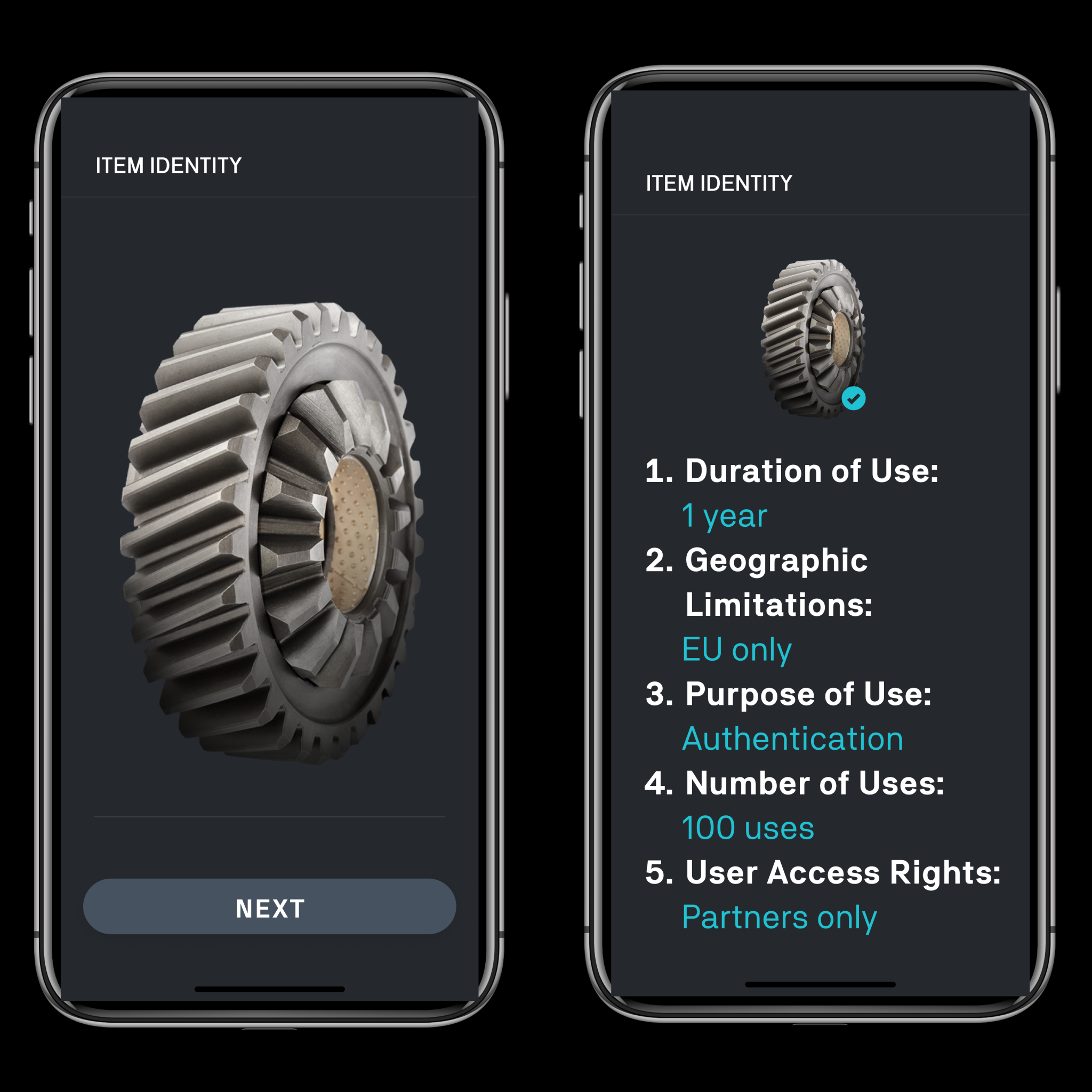
Step 3
Define usage scope based on predefined parameters. -
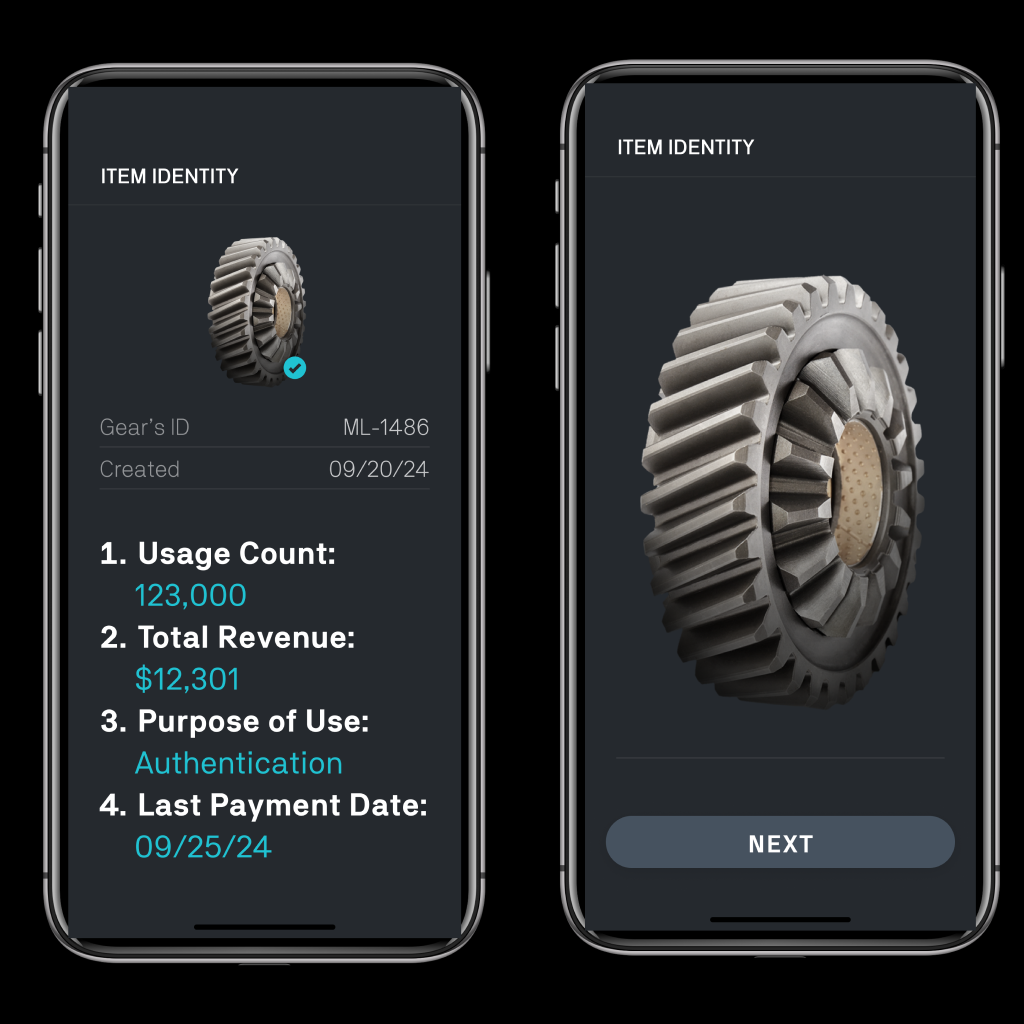
Step 4
Receive revenue and notifications every time your fingerprints are used.
Beware! Avoid the risk of choosing
insecure fingeprinting methods
Even optical and printed features can be counterfeited using advanced techniques, compromising the authenticity of your products. Additionally, blockchain and tokens often struggle to securely link physical items with digital records, making it challenging to ensure true authenticity and integrity.


























